No doubt you’ve heard about the latest Apple security/privacy controversy, whereby it’s been revealed that iPhones, ever since the release of iOS4 last summer, have been automatically and secretly creating a hidden (but unencrypted) file called “consolidated.db,” which keeps a running log of the phone’s location — apparently using cell towers and WiFi network data, not GPS — timestamped down to the second.
There’s no indication that this data is shared with Apple or anyone else (rather, it is simply stored on your phone and, after you sync said phone, your computer), but privacy advocates are nevertheless understandably freaking out, fearing that the data could be accessed and abused by a jealous spouse, a wannabe criminal, the government, or perhaps Apple itself (at some point in the future).
This feature/bug/breach/plot was discovered by a pair of nerds programmers, who have created a free downloadable program that you can use to look at your own location data on a map. Naturally, in keeping with the trend, I couldn’t resist…
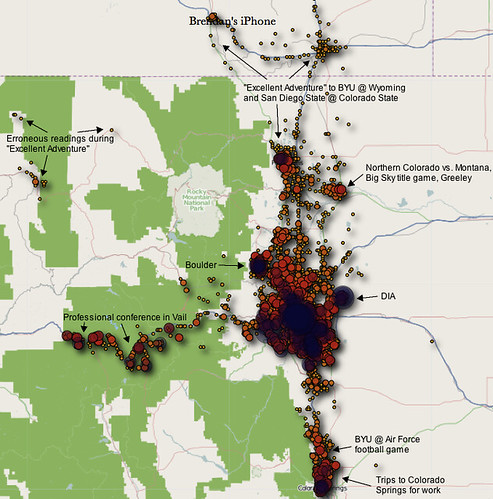
I don’t mind sharing that map (which I’ve helpfully annotated) because, really, you can’t see anything on it that’s particularly private or significant. For instance, you can’t tell exactly where I live, nor even the neighborhood — just that I clearly live somewhere in Denver (duh). Nor does it show any secret travels by yours truly (probably because I don’t have any). It’s pretty unremarkable, really, except for a few basketball and football trips, and professional excursions to Vail and Colorado Springs.
Moreover, what’s really striking about the map is just how freakin’ imprecise it is.
For instance, look at its rendering of my “Excellent Adventure” to Laramie and Fort Collins. You get the general gist that I took the 25 to the 80, passing through Cheyenne and stopping in Laramie (to see The Jimmer, natch). But there are a ton of little dots in the hinterlands north and east of the highway, and along the 287 (the “shortcut” I didn’t actually take), and also some contemporaneous dots in places as far afield as Steamboat Springs (!), that bear no relation to reality.
This incorrect-location issue seems to happen more in areas where service is weak — like Middle of Nowhere, Wyoming — than in other areas. Conversely, there seems to be a distinct bias toward multiple dots clustered in places with comparatively more people and/or better cell service, like Cheyenne (which I merely passed through on the highway, whereas the map would make you think I stopped there and hung out for a while). The same goes for DIA and Boulder, where I’ve certainly spent some time, but not an enormous amount, and yet they appear as huge hubs of locational activity (where the dots are so numerous that, when zoomed out, they combine to form large purple clouds), possibly because they have more cell towers and better service than other, more “in between” places. Mind you, I’m just speculating, but that’s what it seems like.
[UPDATE: I belatedly realized that the map might include Becky’s iPhone’s movements as well, given that I’ve synced her phone on my computer before. If so, that would explain the cluster near Castle Rock — she went to a consignment sale there one time. She’s also spent a lot more time than me in Boulder, due to her product-demoing gig.]
Another thing that’s interesting is how you can clearly see coverage dead zones along the highway. Like the portion of I-80 not quite halfway from Laramie to Cheyenne, and the portion of I-25 just south of the Colorado-Wyoming border. There really is no service there, and you can tell from the map. (Maybe that’s when I was logged as being in Steamboat Springs!)
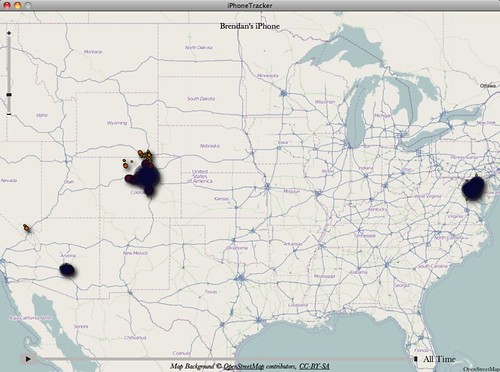
Taking a broader view, you can see I haven’t done too much traveling in the last year or so. I’ve spent tons of time in Colorado, of course; I went to the Washington, D.C. area with Loyacita for Dane’s wedding; I went to Phoenix for Thanksgiving; and I went to Vegas for… wait a minute… what?!? Vegas?!?
Yeah, I have no idea why my iPhone thinks I was in Vegas last July, but that definitely never happened. I guess it must be like the false Steamboat dots (and some other false dots in the Winter Park and Nederland areas, among others). Either that, or I had a reeeeeally good trip to Vegas, and don’t remember a thing about it. #PANIC?! 🙂
Ah well, you know what they say. What happens in Vegas, stays in Vegas. And sometimes, even things that aren’t in Vegas, stay in Vegas, apparently.
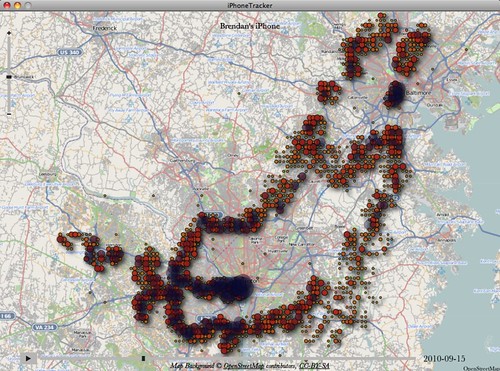
Here’s a closer look at the D.C. trip:
Again, there’s a seeming bias toward big population/cell-signal centers — D.C. proper, Baltimore, and to some extent BWI airport — where I spent comparatively little time compared to other places. And again the “tracking” of my movements is extremely imprecise, giving only a general gist of where I went, not a specific route or exact itinerary.
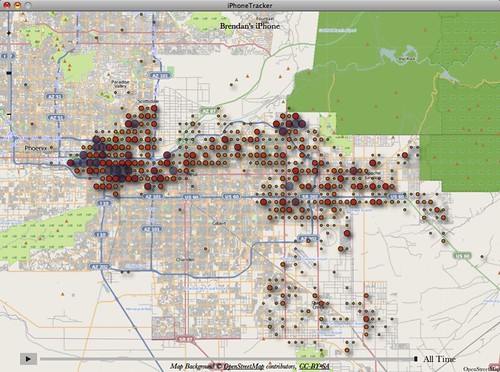
Both of these trends are even more pronounced on the map of my Thanksgiving visit to Arizona:
From that map, you’d think I spent the holiday mostly in the Sky Harbor Airport area and in Mesa. In reality, the comparatively less populated area east of Apache Junction, where Becky’s parents live, is where I was, almost the entire time — yet there are virtually no dots there!
Anyway, I’m not downplaying (or even really commenting on) the severity of significance of the security/privacy issues. I just think it’s fun to look at the maps, and it’s interesting and surprising how imprecise and often simply incorrect (in some cases by many miles) they are.

Personally ive had fun looking at my data. I think it’s an issue that this was stored in so accessible a format without user knowledge, but not a big one. It would be a different thing entirely if the data were being sent back to Apple.
It would be a different thing entirely if the data were being sent back to Apple.
…as far as you know.
In any case, the pervasiveness of technology is only going to grow, which is why I always thought the backlash against Google (and now Apple) has been way overdone.
Some interesting clustering around where I live now, but the clustering around where Bea and I used to live (and where you and Loyacita stayed with us) is oddly fragmented. We had relatively good AT&T coverage though in both locations, so I’m not sure what explains that.
As far as I know? Um, you mean as far as evidence shows that the data is not being transmited at all. There are many techniques to determine what data a given device is transmitting and none of them show that this data is being sent anywhere at all.
What, the Apple fanboi is underestimating the intelligence of Steve Jobs? Muah-hahahahahahaha!
In any case, if Jobs hasn’t figured out how to pull data from iPhones /iOS without consumers knowing, I’m sure someone somewhere in NSA, CIA, or FBI has.
A “professional excursion” to Vail?
Man, did I get into the wrong line of work.
Get a life Andrew. If you can’t argue the points, sure, lets go to name calling. When are you ever going to grow up?
I’m going to second “as far as you know” and throw in a “for now”, and the only name I’m calling you is “David”.
It IS uploaded to your computer when you sync, and I’m pretty sure they can get that data from your computer without your knowledge, unless the system is isolated (no physical connection to the internet, ever, inside a Farraday cage). Off the top of my head, I’d do it during the automatic updating process, or include the file in a program crash report.
And sure, it looks like the data’s not very specific or accurate… yet. In five years, tops, it will be (or would be if the world weren’t ending in 2012).
I just assume the government is tracking my movements, listening to my phone calls, and reading all of my email.
To clarify, so I don’t sound completely paranoid, “the government” means “the Chinese government”, which has cameras pretty much everywhere.
I like to tell myself the American government doesn’t do that stuff.
Doc, my guess is that it is fair to say that, technologically, from an American government perspective, data is captured, but policy restrictions drive what happens to the data. I don’t think the American government is “reading” my emails or “listening” to my phone calls, but I do believe they probably capture that data in some manner as it flows through the information grid; the key is they are forced by policy to let it be filtered out rather than process for further screening and analysis based on my status as a law-abiding American citizen with no criminal history or nexus to any terrorist entities.
I guess what I am saying is that, when it comes to civil liberties and determining what the government ought to be restricted from doing, I think our legal system has acceded to the principle that the restrictions ought to be imposed at the legal or policy level, versus a technological level, lest we inadvertently hamper the government’s ability technologically to defend the country from its enemies and go after bad guys (which is kind of the main point of having a government in the first place).
As I understand the technical limitations of this, root access is required to get this information. So you must have physical access to the phone or access to the machine it syncs with (which is the actual weak point). Unless you’ve jail broken your phone and not changed the password, in which case all bets are off.
Where I see this as a real problem is the police deciding to confiscate someone’s phone and search it without a warrant. Something the politicians will try and argue is completely constitutional because who the hell know why, but it isn’t… And to wit, I wish I could set my phone to self nuke if there are two incorrect passcode attempts not 10.
Loyapalosa! Ahh, yes.
Not sure if a non 3G iPad keeps this file, but this did prompt me to encrypt my backups. Which I should have done a while ago anyways.
It’s not just policy restrictions that keep the gov’t from reading your emails or listening to your phone calls, but practicality. The number of emails and phone calls is just too large for the gov’t to be eavesdropping in any meaningful way — “captured” data or no — absent good cause.
Oddly my iPhone thinks I was in Las Vegas also… Apparently all the iPhones got together and had a party without telling people…
Or else we all got more drunk than we remember the night before your wedding…
OK, that still sounded paranoid. I’m not worried about the Chinese government monitoring me in the US, just here in China. Neither policy restrictions nor sheer numbers protect me here, and I have to be super easy to track by camera. I tend to stand out a bit.
Doc #17 – are you saying that you are the individual who looks like the “1” while those around you look like “o” ? (“to stand out a bit“)
Comment #8 has me wondering if our logonastic David K is also nyctinastic (or even seismonastic) ?
I’m not saying its not impossible for SOMEONE to steal the data from your computer/phone. Obviously its possible, especially if they have physical access, and knowing your locations would be a bad thing, but then if you get your computer/device stolen and its not encrypted they have access to a lot of stuff anyway, not sure your locations over time are the biggest worry.
Yes I think its an issue that this exists without knowledge and is by default unencrypted.
HOWEVER, until there is evidence to show that its actually being USED by Apple and not just as a location cache (Android does it too but purges items older than a given amount of time) it’s wrong to assert that Apple is using the data.
Comment number 18 has me wondering if Alasdair ate paint chips as a child or was dropped on his head repeatedly.
Alasdair, it’s more like O vs i.
The easiest way to get root access – aside from just putting a backdoor in the OS that you’ve written – would be to ask the user for it. “We need to update your program, can we access the internet?” Who says no to that, from Apple?
And sure, there’s no evidence they’re doing anything with the data, nefarious or otherwise. It’s still uncool – imagine the government keeping such info, or maybe asking Apple for it. Collected data is just waiting to be used.
There are 10 kinds of people in the world — those who understand binary and those who don’t.
Hee hee, Joe Mama. Vurragood. 🙂
But being part of the digitally-clueless Zer0-th Majority, I have the following Analogue Age question: WHY IS the locational data-collection In there? Given that it was Unadvertised to the customer, what is its functional purpose? // Is it — as somebody blabbering on my beloved Cablenewsies implied (or, as I Inferred from the Blabber) — somehow a necessary Adjunct to, or unavoidable Byproduct of, the mobile GPS Mapping/Locating/DirectionsFinding apps upon which You Kids Today depend? E.g., I can see that in order to Tell you where to Go, the robot (unlike Me 🙂 needs to know where you Are. But — also where you’ve Been all this past year long??
Ah weel, no matter really. “…there’s no evidence they’re doing anything with the data, nefarious or otherwise. It’s still uncool…” Uncool indeed — and, Evidence, Schmevidence: as always, what Can be done, eventually Will be done.. Personal privacy has been long dead anyway — it didn’t survive the Analogue Age (itself now Of Blessed Memory 😉 and in fact was none too healthy even before that — and like Generalissimo Franco, it’s Still deceased.
This ever-accelerating Digital Information Convergence is but another superfluous Nail in the coffin.
(Here endeth today’s Curmudgeonly Analogue Blabber. 🙂
Venerable Loy – while said robot needs to know where said phone currently is, to plan/display a route to where the phowner wants to go, even for the logonastic amongst us, it has to be a challenge to try to work out reasonable justifications for saving the data … it’s sorta entertaining watching the iColytes try to justify it, I’ll admit …
Personal privacy, however, has become more and more dependent upon the Purloined Letter techniques …
Esteemed Alasdair: Aye.
Pingback: IntraCleanse Reviews
Pingback: cheap oil change